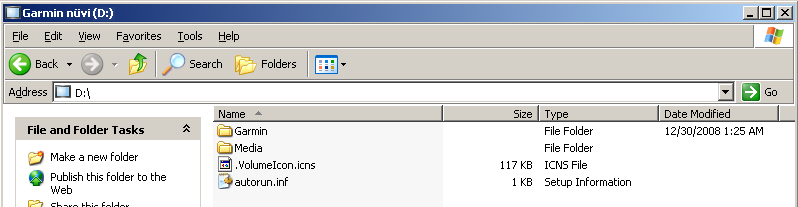
As you’ll recall from my Christmas post the company I work for is replacing their fleet management equipment, and in part that means upgrading some of our older Garmin GPS screens. As a result a steady stream of old equipment has been trickling into my office.
Even though these units no longer fit our needs, there is still plenty of life left to them.
Science!
Wikipedia states that “forensic science is the scientific method of gathering and examining information about the past“, our methods might not be too scientific, but these devices are chock-full of information about the past.
In preparation for finding them new homes, I thought it might be wise to see what kind of private data these things have stored. I came across a nice overview presentation on GPS forensics that covers a variety of models and brands. That presentation listed some files of interest:
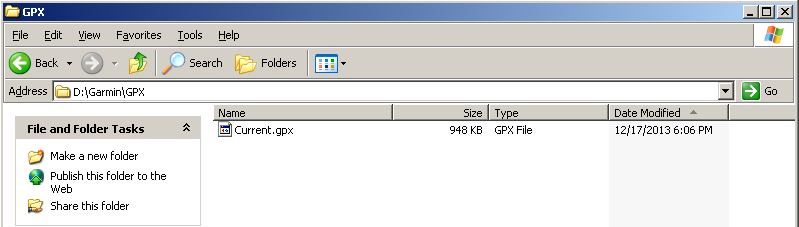
Current.gpx
Archive.gpx
Position.gpx
GarminDevice.xml
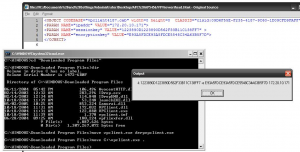
After connecting the Garmin to a computer and waiting for the Garmin’s operating system to start I was able to see the Garmin as a storage device.
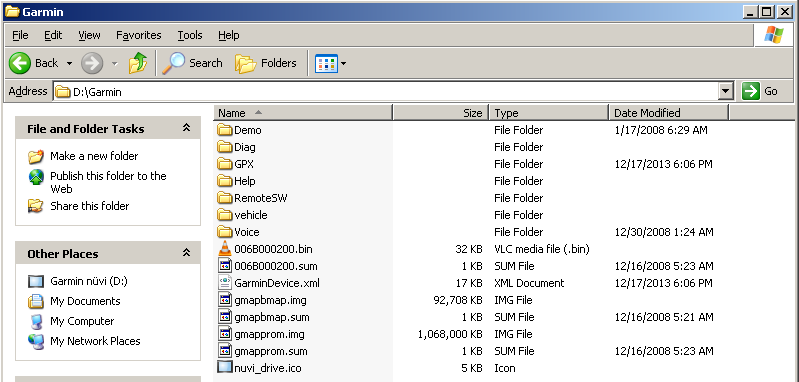
Navigating to the \Garmin\GPX directory I was able to locate Current.gpx.
GPX Format
The GPX in the GPX file format stands for GPS eXchange Format. It’s a fairly simple XML format with plenty of human readable items of interest. Here are some (slightly sanitized) snippets from the GPX file I recovered to give you an idea of the format. The file I was working with was devoid of line breaks, but I’ve added some here for clarity.
After a quick header we get into some more interesting stuff.
<gpx xmlns="http://www.topografix.com/GPX/1/1" xmlns:gpxx="http://www.garmin.com/xmlschemas/GpxExtensions/v3" xmlns:gpxtpx="http://www.garmin.com/xmlschemas/TrackPointExtension/v1" creator="nüvi 5000" version="1.1" xmlns:xsi="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation="http://www.topografix.com/GPX/1/1 http://www.topografix.com/GPX/1/1/gpx.xsd http://www.garmin.com/xmlschemas/GpxExtensions/v3 http://www.garmin.com/xmlschemas/GpxExtensionsv3.xsd http://www.garmin.com/xmlschemas/TrackPointExtension/v1 http://www.garmin.com/xmlschemas/TrackPointExtensionv1.xsd">
The “metadata” section seems pretty boring. I think the time listed here is the last time the unit was used.
<link href="http://www.garmin.com">
<text>Garmin International</text>
</link>
<time>2014-01-16T21:44:20Z</time>
</metadata>
Now on to some good stuff, Waypoints.
<ele>241.17</ele>
<name>001</name>
<sym>Waypoint</sym>
</wpt>
Some Waypoint entries contain “extensions”, these might include Address Book entries
<gpxx:WaypointExtension>
<gpxx:Categories>
<gpxx:Category>Address Book</gpxx:Category>
</gpxx:Categories>
Or just addresses
<gpxx:WaypointExtension>
<gpxx:Address>
<gpxx:StreetAddress>101 W. Flagler St</gpxx:StreetAddress>
<gpxx:City>Miami</gpxx:City>
<gpxx:State>FL</gpxx:State>
<gpxx:Country>USA</gpxx:Country>
<gpxx:PostalCode>33130</gpxx:PostalCode>
</gpxx:Address>
</gpxx:WaypointExtension>
</extensions>
Far more interesting than the Waypoints however is the Tracks log. This data is a series of positions at a given time which leaves a trail of breadcrumbs which we can use to reconstruct the journey.
Here is part of one particular journey
<name>ACTIVE LOG: 08 JAN 2014 12:06</name>
<trkseg>
After the “trkseg” element begins a series of coordinates, elevations, and times follow
<ele>196.25</ele>
<time>2014-01-08T17:06:41Z</time>
</trkpt>
<trkpt lat="23.884317" lon="-81.686580">
<ele>196.73</ele>
<time>2014-01-08T17:06:43Z</time>
</trkpt>
<trkpt lat="23.884317" lon="-81.686580">
<ele>196.73</ele>
<time>2014-01-08T17:06:44Z</time>
</trkpt>
<trkpt lat="23.884317" lon="-81.686580">
<ele>196.73</ele>
<time>2014-01-08T17:06:45Z</time>
</trkpt>
…And so on
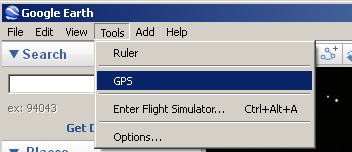
Google Earth
As you can see this information is easy to work with to suit your needs. If your needs are just to watch what happened and when, Google Earth is great tool for this. It turns out Google Earth already understands the GPX format, so we don’t need to extract any data manually.
Select the Import from file option followed by the Import button
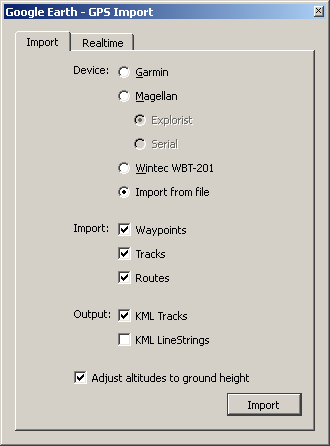
Navigate to your Current.gpx file (in my case \Garmin\GPX), select it and click Open
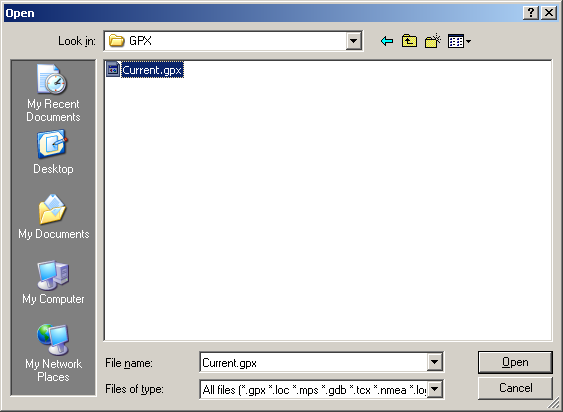
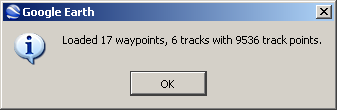
Google Earth will tell you what data it was able to find. Click OK
On the left panel you can move between waypoints to see them on the map.
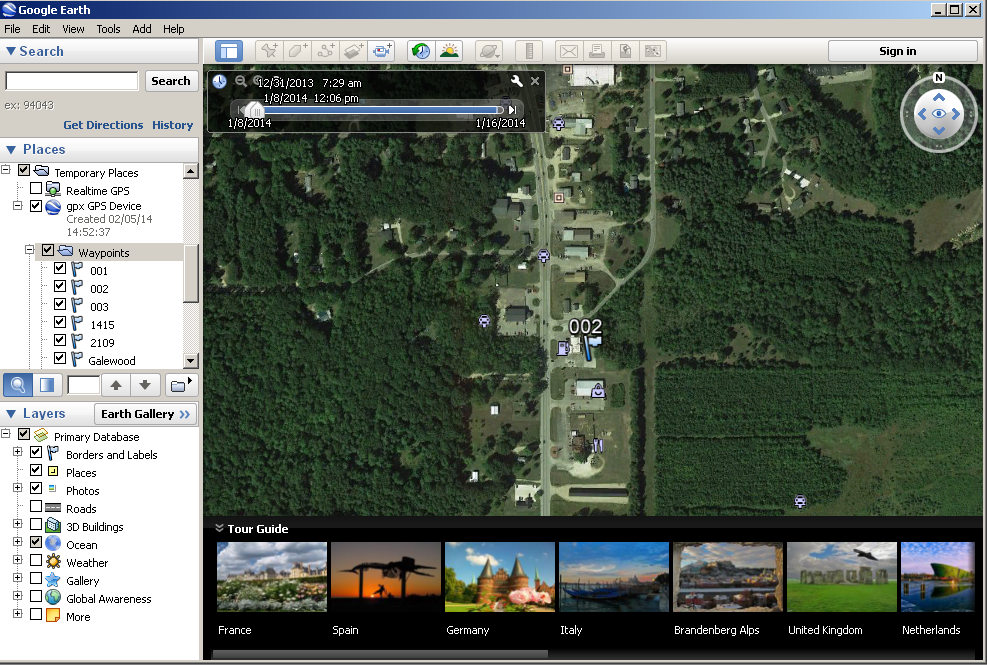
Fun
For even more fun, select one of the “Tracks” logs, and click the play button with breadcrumb icon (I assume that’s what that is anyhow).
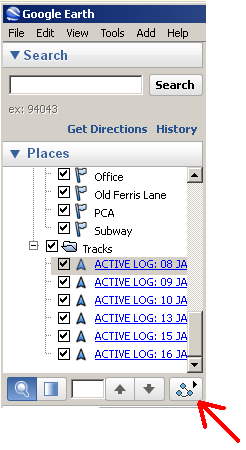
Here is some sample video I captured from the playback of some track log data. The data isn’t real-time of course (that would be boring), but there is still some relevant timing preserved. Notice how you can even tell which stop lights were red by the time elapsed between movements. Very interesting and potentially revealing stuff.